Mobile app cryptography stands as a crucial pillar in safeguarding sensitive information in our increasingly digital world. An alarming analysis by Zimperium zLabs revealed that an astounding 92% of mobile applications, including 56% of the top 100 apps, employ flawed cryptographic methods, exposing countless users to significant risks. The revelations indicate a startling rise in cryptography vulnerabilities, with high-severity issues such as hardcoded keys compromising data protection efforts. As enterprise mobile applications become integral to daily operations, the necessity for robust mobile app security has never been more urgent. With the projected financial losses due to data breaches reaching $280 billion in 2024, enhancing cloud storage security and protecting users’ personal data must take center stage.
When we talk about the protection of sensitive data within mobile software, we delve into the realm of application encryption and digital security mechanisms. Recent findings have cast a spotlight on the vulnerabilities inherent in many widely used mobile applications, pinpointing crucial failures in their cryptographic protocols. The rise of exploitative methods reveals a pressing need for organizations to bolster their data safeguarding techniques, as reliance on outdated security frameworks can spell disaster. Utilizing advanced encryption standards can significantly enhance the security of enterprise mobile applications and mitigate risks associated with cloud storage. It’s evident that improved cryptography practices are essential for ensuring the integrity and confidentiality of user data in a cloud-connected ecosystem.
Understanding Cryptography Vulnerabilities
Cryptography vulnerabilities represent a critical risk to mobile app security, particularly for enterprise applications. As revealed in Zimperium zLabs’ analysis, a staggering 92% of mobile applications contained compromised cryptographic methods. Issues such as hardcoded keys and the use of outdated algorithms significantly increase the probability of data breaches, hence undermining the integrity of data protection protocols. Flawed encryption methods can be exploited by attackers, leading to severe penalties for organizations in terms of financial losses and reputational damage.
Moreover, the increasing sophistication of cyber threats amplifies the need for robust cryptographic measures. The data presented underscores the urgency for developers to adopt modern encryption techniques that safeguard user data against unauthorized access. As malicious entities become more adept at exploiting these vulnerabilities, organizations must prioritize cryptography in their security strategies to protect sensitive information and uphold their customers’ trust.
The Importance of Mobile App Security
Mobile app security is paramount, particularly as mobile devices often serve as gateways to critical digital services. The findings from Zimperium highlight significant lapses in security, with 56% of the top mobile apps exhibiting features that compromise user data. For example, many applications inconsistently implement security measures, leaving gaps for cybercriminals to exploit. A commitment to robust mobile app security not only protects enterprise data but also fortifies user confidence in these digital platforms.
As mobile applications continue to proliferate within enterprise environments, organizations must conduct regular security assessments to identify and rectify potential vulnerabilities. Tools and best practices centered on mobile app security should be integrated into the app development life cycle, ensuring compliance with industry standards and regulations. Enhancing mobile app security can mitigate risks and safeguard user data against breaches.
Frequently Asked Questions
What are common cryptography vulnerabilities in mobile apps?
Mobile app cryptography vulnerabilities often include the use of outdated algorithms, hardcoded cryptographic keys, and improper key management. As revealed by Zimperium zLabs, a staggering 92% of apps, including many enterprise mobile applications, utilize flawed cryptographic methods that can expose sensitive data and increase the risk of data breaches.
How can I enhance mobile app security using cryptography?
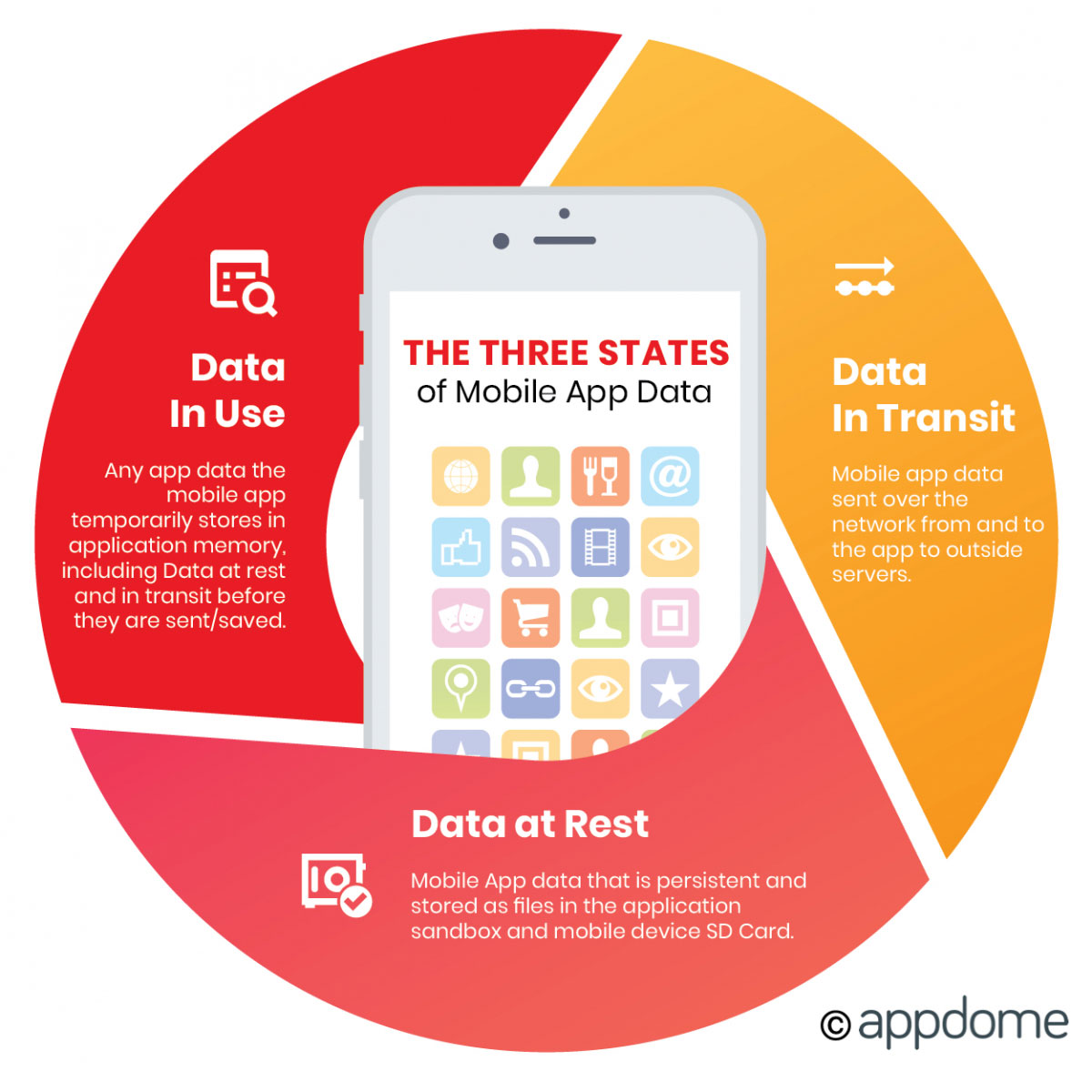
To enhance mobile app security, developers should implement strong cryptographic practices such as utilizing modern algorithms, ensuring proper key management, and regularly updating security protocols. Encrypting data both at rest and in transit is essential, as is continuously assessing the app for cryptography vulnerabilities to protect against potential exploitation.
What role does cryptography play in data protection for mobile applications?
Cryptography plays a crucial role in data protection for mobile applications by safeguarding sensitive user information through encryption. This ensures that data transmitted between mobile devices and servers remains confidential, thereby reducing the risk of unauthorized access or data breaches that can lead to significant financial and reputational harm.
How does cloud storage security relate to mobile app cryptography?
Cloud storage security is integral to mobile app cryptography, as unprotected or misconfigured cloud services can lead to data exposure. Zimperium’s findings indicate that many popular mobile apps fail to secure data stored in the cloud properly, highlighting the need for robust cryptographic measures to protect data stored on cloud platforms from unauthorized access.
What is the impact of cryptography weaknesses on enterprise mobile applications?
Cryptography weaknesses in enterprise mobile applications can lead to unauthorized access, data leakage, and significant financial losses. With many apps relying on outdated cryptographic methods, organizations risk exposing sensitive information, which can result in legal ramifications and damage to trust and credibility in the market.
What are the challenges in ensuring secure cryptographic practices in mobile apps?
Challenges in ensuring secure cryptographic practices in mobile apps include the rapid evolution of threats, the complexity of implementing robust security measures, and the need for constant updates to cryptographic algorithms. Moreover, the prevalence of hardcoded keys and outdated practices further complicates mobile app security, making it vital for developers to stay informed on best practices.
How can enterprises audit mobile app cryptography practices effectively?
Enterprises can audit mobile app cryptography practices effectively by conducting comprehensive security assessments regularly, utilizing automated tools for vulnerability scanning, and reviewing code for hardcoded keys and outdated algorithms. Engaging with security experts can also help identify potential weaknesses and ensure compliance with best practices to maintain robust mobile app security.
| Key Point | Details |
|---|---|
| High Percentage of Flawed Apps | 92% of all mobile apps analyzed use flawed cryptographic methods. |
| Top 100 Apps Vulnerabilities | 56% of the top 100 apps have flawed cryptography, with 5% showing high-severity vulnerabilities. |
| Personal Data Compromise | In 2024, 1.7 billion people’s data was compromised, a 312% increase from 2023. |
| Financial Loss | Estimated financial loss due to data compromise reached $280 billion. |
| Cloud Storage Risks | 83 Android apps with misconfigured or unprotected cloud storage. |
| Exposed AWS Credentials | 10 apps had exposed AWS credentials potentially allowing full access to sensitive data. |
Summary
Mobile app cryptography is paramount for ensuring the security and privacy of users in an increasingly digital landscape. With over 92% of mobile applications identified as using flawed cryptographic practices, the risks for organizations are significant. As personal and sensitive data continues to be targeted, effective cryptographic measures are vital to prevent breaches and data compromises that could lead to severe financial and reputational losses. Organizations must prioritize the implementation of robust and secure cryptographic methods to safeguard their applications and build trust with their users.