Mobile security threats are an escalating concern that organizations can no longer afford to overlook. As reliance on smartphones, tablets, and laptops increases in the workplace, the prevalence of cyber threats like mobile phishing and malware attacks continues to rise. According to recent analyses, attackers are adopting mobile-first strategies that circumvent traditional cybersecurity defenses, placing sensitive data at risk. With 70% of companies adopting BYOD security frameworks, safeguarding mobile application security has become paramount in protecting both corporate and personal information from malicious interference. To counteract these threats, businesses must implement robust mobile security measures to mitigate the impact of cybercriminal activities.
The landscape of mobile cybersecurity is fraught with challenges as companies navigate the vulnerabilities posed by mobile devices and applications. Organizations must remain vigilant against emerging threats associated with handheld technology, particularly those arising from mobile phishing attacks, which compromise user information through deceptive tactics. A comprehensive approach to safeguarding mobile endpoints is essential, as cyber threats evolve rapidly and target enterprises’ digital operations. With the increasing popularity of BYOD policies, attention to mobile application safeguards and overall defense strategies is crucial in maintaining organizational integrity. As such, businesses are called to embrace advanced mobile security frameworks that anticipate and respond to these evolving risks.
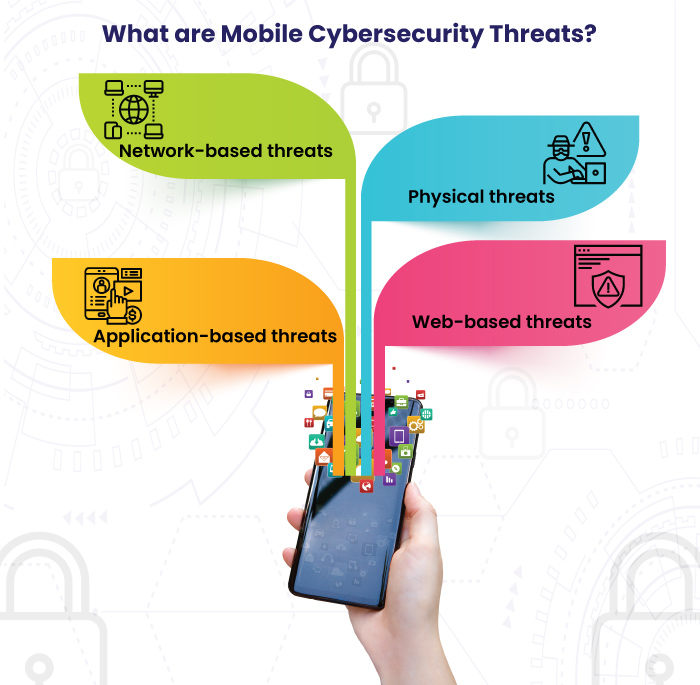
Understanding Mobile Security Threats
Mobile security threats are a critical concern for organizations that rely on mobile devices for daily operations. High-profile breaches underscore how attackers are taking advantage of vulnerabilities in devices and applications. With the vast majority of companies embracing mobile technology for productivity and customer engagement, the risks associated with mobile security have escalated, warranting urgent attention and action from IT departments. Security measures that once sufficed are no longer adequate against mobile-first attack strategies crafted by cybercriminals.
Organizations need to understand that mobile threats are not just random nuisances but well-planned attacks on critical data. Cybersecurity experts continuously advocate for advanced measures, including robust BYOD security policies and stringent application security protocols, to defend against malicious activities. It’s vital for companies to not only employ traditional security measures, but also incorporate sophisticated defenses tailored to the distinctive traits of mobile ecosystems.
The Rise of Mobile Phishing Attacks
Mobile phishing, commonly known as “mishing,” has become a rampant threat in the digital landscape. The rise in smishing, which leverages SMS for fraudulent activities, is alarming—accounting for a staggering 69.3 percent of all mishing incidents as reported by Zimperium zLabs. As more employees access company data from mobile devices, the risk of falling victim to these deceptive tactics increases, necessitating educational initiatives for users to recognize the signs of phishing attempts.
Apart from smishing, new attack vectors such as PDF phishing are emerging, threatening to expand the scope of mobile phishing. Cybercriminals are becoming more sophisticated, using SMS and email to lure individuals into sharing sensitive information unwittingly. Furthermore, voice phishing, or vishing, has also gained traction, with significant increases in reported attacks showcasing how diverse and adaptive these threats have become.
Defending Against Malware Attacks on Mobile Devices
Malware attacks are a persistent menace that continues to target mobile devices. Zimperium’s latest report highlights a staggering 50 percent year-over-year increase in the deployment of Trojans—specifically designed malware that infiltrates unsuspecting devices. These malicious software programs can lead to data breaches and severe disruptions, as users may inadvertently install harmful applications from unverified sources, which underscores the importance of malware awareness and educational programs.
Companies must implement comprehensive malware defenses to combat this growing threat. This includes employing mobile application security measures to ensure that apps developed for internal and external stakeholders are safeguarded against vulnerabilities. Regular assessments and monitoring can help organizations identify and neutralize potential risks before they escalate into more significant security incidents.
Application Security: A Critical Component of Mobile Security
Mobile application security is crucial in protecting sensitive organizational data from cybercriminals. Internally developed applications, particularly those used by employees and clients, can be targets for reverse engineering and exploitation if adequate security measures are not in place. Companies must prioritize security at every stage of application development to ensure they are not introducing vulnerabilities that could be exploited.
The inherent risk of allocating sensitive functions to mobile apps necessitates an ongoing commitment to security throughout the app’s lifecycle. This includes thorough testing, regular updates to patch vulnerabilities, and ensuring adherence to best practices in application design. By cultivating a mindset oriented towards security, enterprises can significantly reduce their exposure to potential mobile threats.
The Importance of BYOD Security Policies
With the growing trend of Bring Your Own Device (BYOD) in workplaces, establishing stringent BYOD security policies has never been more critical. As employees access corporate networks and sensitive data on their personal devices, the potential for security breaches increases exponentially. BYOD security measures must encompass data encryption, remote wiping capabilities, and secure access protocols to mitigate risks associated with personal devices.
Additionally, organizations should develop comprehensive training programs to instruct employees on safe practices when using personal devices for work-related tasks. This includes recognizing social engineering tactics like mobile phishing and ensuring that all applications and software are regularly updated. A proactive approach not only fosters a security-conscious work culture but also significantly strengthens the organization’s defense against cyber threats.
Navigating the Mobile Threat Landscape
To successfully navigate the dynamic mobile threat landscape, businesses must adopt a holistic approach to mobile security that encompasses real-time threat visibility and comprehensive protection. As noted by cybersecurity expert Kern Smith, understanding the ever-evolving tactics of attackers is crucial. Only then can organizations implement effective strategies to mitigate risks associated with mobile technology.
A multi-layered defense strategy that includes continuous monitoring, regular vulnerability assessments, and incident response plans is essential. Organizations must remain vigilant and adaptable, employing advanced threat detection methodologies to stay one step ahead of cybercriminals who adapt their techniques rapidly. This level of preparedness is vital to safeguarding sensitive information and ensuring business continuity.
The Role of Employee Training in Mobile Security
Employee training is a paramount element of a successful mobile security strategy. Cybersecurity threats, particularly mobile phishing and malware attacks, often exploit human error. By equipping employees with the knowledge and tools needed to recognize suspicious activities and maintain safe practices, organizations can effectively reduce the likelihood of breaches. Tailored training programs that focus on common mobile threats can be especially effective.
Regular refresher courses can ensure that employees stay updated on the latest security practices and threat vectors. Additionally, fostering a culture of security awareness encourages employees to take ownership of their role in safeguarding sensitive data. The more educated employees are about the risks and protective measures, the less vulnerable the organization becomes to mobile security threats.
Evaluating Third-Party Mobile Applications
As organizations leverage third-party mobile applications for enhanced productivity, the risks associated with these external applications need thorough evaluation. Many organizations underestimate the threats posed by unvetted applications that can serve as gateways for malware and other security vulnerabilities. A comprehensive evaluation process must include assessing application security protocols and ensuring compliance with industry standards.
Organizations should not adopt third-party applications lightly; conducting risk assessments that include vulnerability scanning and penetration testing can list potential concerns. Ensuring that applications are regularly updated and supported by the vendor can further reduce risks associated with external tools used within the organizational framework.
Implementing Comprehensive Mobile Security Strategies
A robust mobile security strategy is essential in defending organizational assets against a rapidly evolving threat landscape. This approach should encompass various components including data encryption, mobile threat detection, and incident response capabilities. Enterprises must recognize that their mobile security needs are unique, requiring tailored strategies that address specific vulnerabilities associated with mobile devices and applications.
Successful implementation involves a collaborative effort across departments, ensuring that IT and security teams work together to establish best practices for mobile security. Devising policies that clearly outline acceptable use, coupled with ongoing monitoring and adjustments based on emerging threats, can create a resilient posture against cyber threats targeting mobile environments.
Frequently Asked Questions
What are the main types of mobile security threats targeting devices today?
Mobile security threats primarily include mobile phishing (also known as mishing), malware attacks, and vulnerabilities in mobile application security. Cybercriminals increasingly utilize tactics like SMS phishing (smishing) and voice-call phishing (vishing) to exploit users. Additionally, malware such as Trojans has seen a significant rise, making it crucial for organizations to implement robust BYOD security measures.
How does mobile phishing (mishing) affect mobile device security?
Mobile phishing, or mishing, poses a significant risk to mobile device security by tricking users into providing sensitive information through deceptive messages, especially via SMS. With smishing accounting for 69.3 percent of mishing incidents, it highlights the need for comprehensive mobile security strategies that educate users and utilize protective measures against such threats.
What role does BYOD security play in protecting against mobile security threats?
BYOD security is essential in protecting against mobile security threats as more organizations allow employees to use personal devices for work. Effective BYOD policies should include mobile application security protocols, regular training on recognizing phishing attempts, and ensuring that all mobile devices accessing company networks are equipped with security solutions to mitigate malware and other threats.
Why is mobile application security critical in preventing malware attacks?
Mobile application security is critical in preventing malware attacks because vulnerable applications can be an entry point for cybercriminals to implant Trojan malware. Applications that aren’t rigorously evaluated for security flaws can lead to sensitive data leakage, reinforcing the need for comprehensive testing before deployment.
What are the common signs of a mobile malware attack?
Common signs of a mobile malware attack include the device performing unusually slow, unexpected app crashes, excessive data usage, and the presence of unfamiliar applications. Recognizing these symptoms early can help users and organizations respond quickly to mitigate damage and enhance overall mobile security.
How can organizations enhance their defenses against mobile security threats?
Organizations can enhance their defenses against mobile security threats by adopting a holistic mobile security strategy that incorporates real-time threat intelligence, user training on recognizing phishing attempts, and a proactive approach to mobile application security. Regular updates and security assessments of mobile applications and ensuring robust BYOD security are also essential components.
What impact do Trojans have on mobile security?
Trojans significantly impact mobile security as they can disguise themselves as legitimate applications, giving cybercriminals access to sensitive data. With a 50 percent year-on-year increase in Trojan use, especially in banking applications, it is vital for organizations to implement strict security measures and educate users on safe downloading practices.
How does the shift to mobile-first attack strategies affect cybersecurity?
The shift to mobile-first attack strategies affects cybersecurity by introducing new vulnerabilities that traditional security measures may not address. As attackers target organizations that use mobile technology for productivity, there is an urgent need for enterprises to develop comprehensive mobile security strategies that encompass both devices and applications to prevent data breaches.
| Key Point | Details |
|---|---|
| Mobile Security Threats | Mobile threats are rapidly evolving and target organizational endpoints. |
| Increase in Mobile Phishing | Mobile phishing attacks (mishing) have increased, with smishing (SMS-based phishing) constituting 69.3% of incidents. |
| Malware Trends | Trojans are the most common malware types, with a 50% annual increase noted in their use. |
| Vulnerability of Internally Developed Apps | Custom mobile applications may lack necessary defenses and can be exploited by attackers. |
| Strategic Response Required | A comprehensive mobile security strategy is essential for protecting sensitive data against evolving threats. |
Summary
Mobile security threats are a significant concern in today’s hybrid work environment, requiring organizations to adopt robust security measures. With attackers increasingly targeting mobile devices and employing mobile-first strategies, companies must prioritize comprehensive mobile security strategies that include both devices and apps. Real-time threat visibility and protection are crucial for safeguarding sensitive data from sophisticated mobile phishing, malware, and other cyber threats.