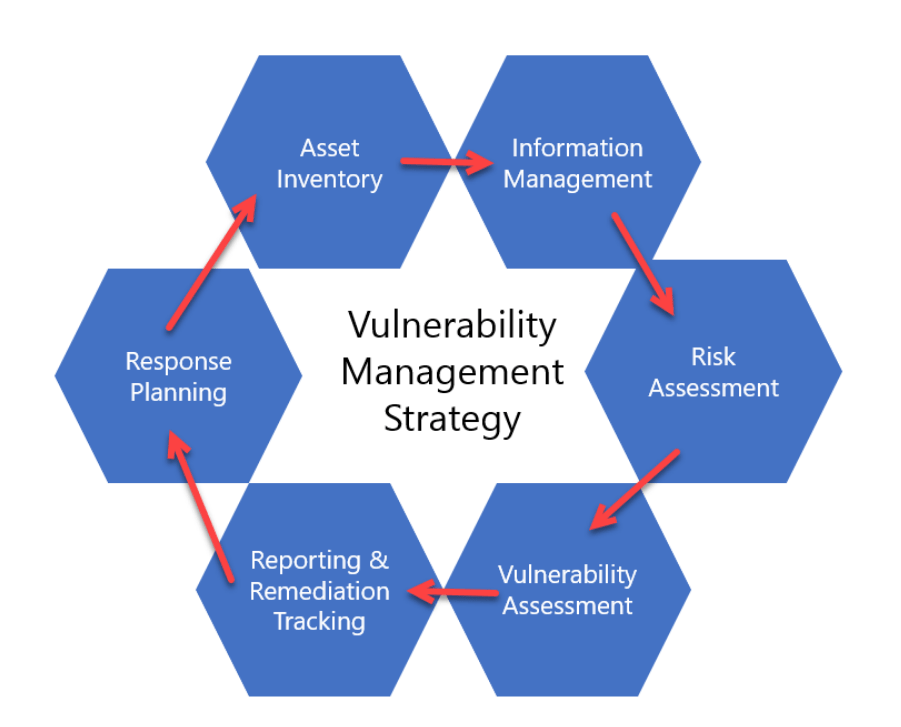
Vulnerability management is becoming a crucial pillar of enterprise risk management as organizations strive to secure their digital environments effectively. Recent insights reveal a significant shift from merely addressing every discovered vulnerability to a more strategic approach that emphasizes risk prioritization and business impact. In fact, a staggering 73% of organizations recognize the need for solutions that contextualize risks within their IT landscape, and 45% are seeking new tools to enhance their vulnerability exposure assessments. This proactive stance is driven by a recognition that most cybersecurity threats come from older, overlooked vulnerabilities that are more susceptible to exploitation, accentuating the importance of threat intelligence. By adopting a modern cybersecurity strategy that balances remediation efforts with real-time insights, organizations can significantly mitigate their risk and bolster their defenses against potential breaches.
When we discuss the safeguarding of digital assets, terms like risk assessment and threat management often come to mind alongside vulnerability management. This approach involves identifying weaknesses in systems and applications while prioritizing them based on their potential impact on organizational objectives. Many enterprises are now focusing on enhancing their overall risk posture through more insightful exposure management practices, leveraging threat intelligence to inform their strategies effectively. By transitioning from a reactive to a proactive framework, organizations can better manage their cybersecurity risks and align their mitigation strategies with business priorities. Overall, the evolution of vulnerability oversight reflects a growing understanding of the need for a comprehensive approach to enterprise safety.
The Importance of Vulnerability Management in Cybersecurity Strategies
Vulnerability management has become a cornerstone of effective cybersecurity strategies for organizations. As cyber threats evolve, focusing on vulnerability management enables enterprises to identify, assess, and respond to security weaknesses before they can be exploited. The importance of this proactive approach cannot be overstated, particularly as reports indicate that most critical threats emerge from older, overlooked vulnerabilities. By integrating vulnerability management into overall enterprise risk management (ERM) frameworks, organizations can ensure they’re prioritizing risks that matter most to their specific operational context.
Moreover, the ability to prioritize vulnerabilities according to risk level is essential for robust incident response. Organizations that incorporate threat intelligence and real-time visibility into their vulnerability management processes are far better positioned to defend against active threats. As noted by cybersecurity experts, simply relying on CVSS scores can create a false sense of security, which is why adopting a risk-based approach that reflects actual threat landscape and business impact is critical. This is where effective vulnerability management truly shines, allowing companies to focus on the vulnerabilities that pose the highest risk to their assets and operations.
Enhancing Visibility into Vulnerability Exposure for Better Risk Management Strategies in Enterprises
Visibility into vulnerability exposure is elemental for effective enterprise risk management. Organizations are increasingly recognizing the necessity of this visibility and are consequently investing in advanced vulnerability management solutions that can provide insights into potential exploitation risks. A recent study revealed that 44 percent of organizations are keen on improving their understanding of real-time vulnerability exposure as a critical step towards better managing their risk profile. This emphasis on visibility aids not only in prioritizing vulnerabilities but also in formulating a strategic response framework based on a comprehensive understanding of the potential threats.
Furthermore, achieving a clear picture of vulnerability exposure goes hand-in-hand with enhancing risk prioritization. Organizations are urged to leverage threat intelligence, which offers insights into active exploitation tactics and assists in assessing the criticality of their IT assets. Decision-makers are advised to integrate this intelligence into their risk assessment processes, which can dramatically refine their vulnerability management strategies. By focusing on high-risk areas that pose a significant threat to business continuity or compliance requirements, organizations can allocate resources more effectively and bridge the gap between technology, operations, and risk management.
Adopting a Risk-Based Approach to Vulnerability Management and Patching
Transitioning to a risk-based approach for vulnerability management is becoming increasingly essential for organizations striving to enhance their cybersecurity posture. Many enterprises are realizing that ineffective patching strategies, dependent solely on CVSS scores, lead to instances of high-risk vulnerabilities remaining unaddressed. A risk-based methodology not only prioritizes vulnerabilities in terms of real-world exploitability but also aligns remediation efforts with business objectives. This allows organizations to justify investments in cybersecurity measures by directly correlating them to their risk tolerance and operational needs.
In implementing a risk-based strategy, incorporating threat intelligence becomes paramount. Decision-makers must leverage intelligence that identifies which vulnerabilities are actively being exploited in the wild, shifting their focus from merely patching gaps to understanding how vulnerabilities impact critical assets and their configurations. Aligning vulnerability management with active threat indicators allows organizations to make informed decisions on which vulnerabilities to remediate first, ultimately driving more effective security outcomes and reducing overall risk exposure.
Budgeting for Effective Vulnerability Management Solutions in the Modern Threat Landscape
As illustrated in recent findings, there is a clear trend towards increased budgets for vulnerability management solutions amongst organizations, with 84 percent of enterprises expressing a willingness to significantly enhance their spending. This investment trend underscores the urgency placed on maintaining robust defenses against escalating cyber threats. Businesses are not only looking to adopt new technologies but also to refine their existing cybersecurity strategies to withstand increasingly sophisticated attacks.
Allocating resources towards effective vulnerability management solutions reflects a growing recognition of the fact that traditional approaches are no longer sufficient. Organizations should prioritize investing in platforms that incorporate advanced analytics to assess vulnerabilities in the context of their specific operational environments. This ensures that organizations are not merely checking boxes but are instead proactively managing their risk exposure and continuing to protect sensitive data and infrastructure amid a quickly shifting cybersecurity landscape.
Frequently Asked Questions
What is the importance of vulnerability management in enterprise risk management?
Vulnerability management plays a critical role in enterprise risk management by identifying, assessing, and prioritizing vulnerabilities within an organization’s IT infrastructure. Effective vulnerability management helps organizations mitigate risk by focusing on the most critical vulnerabilities that pose a real threat to their systems and data, thus enhancing overall cybersecurity strategy.
How does risk prioritization affect vulnerability management?
Risk prioritization is essential in vulnerability management as it allows organizations to allocate resources effectively to the vulnerabilities that matter most. By prioritizing risks based on factors such as exploitability, asset criticality, and threat intelligence, organizations can ensure that they address the vulnerabilities that could have the highest impact on their business, rather than simply patching based on CVSS scores.
What are the challenges organizations face in achieving vulnerability exposure visibility?
Organizations often encounter significant challenges in achieving vulnerability exposure visibility due to outdated systems, a lack of integration between security tools, and insufficient threat intelligence. Surprisingly, while many recognize the need for improved visibility, 81 percent of organizations reported difficulties in tracking real-time vulnerability exposure and risk levels, complicating their ability to respond effectively.
Why is threat intelligence critical for effective vulnerability management?
Threat intelligence is critical for effective vulnerability management because it provides context about the current threat landscape, including information on active exploits and known threat actor groups. By integrating threat intelligence into their vulnerability management processes, organizations can better prioritize vulnerabilities that are actively being targeted, thus improving their defense strategies and overall cybersecurity posture.
How can organizations accelerate the remediation process for vulnerabilities?
Organizations can accelerate the remediation process for vulnerabilities by adopting a modern, risk-based approach to vulnerability management. This involves leveraging automation, integrating threat intelligence, and focusing on real-world exploitability to prioritize remediation efforts on vulnerabilities with the highest potential impact on business operations.
What are the key factors decision-makers consider when assessing risk in vulnerability management?
When assessing risk in vulnerability management, decision-makers typically consider factors such as the internet reachability of vulnerable assets (62 percent), threat intelligence indicating active exploitation (58 percent), and the criticality of the IT asset to business operations (55 percent). These factors help in identifying which vulnerabilities to address promptly.
How are organizations planning to enhance their vulnerability management practices in the near future?
Organizations are looking to enhance their vulnerability management practices by increasing their budgets and adopting new exposure management solutions. According to recent reports, 84 percent of enterprises are boosting their vulnerability management budgets, and 95 percent are likely to implement new platforms within the next year, reflecting a proactive approach to managing vulnerabilities and reducing risk.
| Key Point | Details |
|---|---|
| Evolving Focus in Risk Management | Transitioning from a volume-based approach to a value-based approach, addressing critical vulnerabilities instead of fixing everything. |
| Critical Threats are Rare | Only 1 in 50,000 vulnerabilities is considered a critical threat; those often overlooked are usually older and less visible. |
| Prioritization in Vulnerability Management | 73% of respondents believe solutions should prioritize risks according to IT context; 81% face challenges in achieving this. |
| Adopting New Solutions | 45% of organizations aim to adopt new solutions primarily for better risk prioritization. |
| Importance of Real-time Visibility | Nearly half (44%) desire better visibility into real-time vulnerability exposure and risk levels. |
| Accelerating Remediation Efforts | Organizations want to swiftly address the most impactful vulnerabilities (40%). |
| Current Practices Leading to False Security | Relying solely on CVSS scores for prioritization can create a false sense of security, according to industry experts. |
| Risk Assessment Prioritization Criteria | Decision-makers prioritize based on reachability, active exploitation intelligence, and business criticality. |
| Budget Increases for Vulnerability Management Solutions | 84% of enterprises are increasing their vulnerability management budgets and exploring new platforms (95% likelihood of adopting in 12 months). |
Summary
Vulnerability management is increasingly vital as organizations strive to protect their assets from critical threats. The trends indicate a significant shift toward prioritization based on business context and real exploitability of vulnerabilities. With most critical vulnerabilities being a rarity and often overlooked, a risk-based approach to vulnerability management that focuses on real-time visibility and accelerated remediation is essential for enhancing enterprise security. Organizations are eager to adopt more effective vulnerability and exposure management solutions, with a notable increase in their budgets aimed at improving this crucial aspect of cybersecurity.