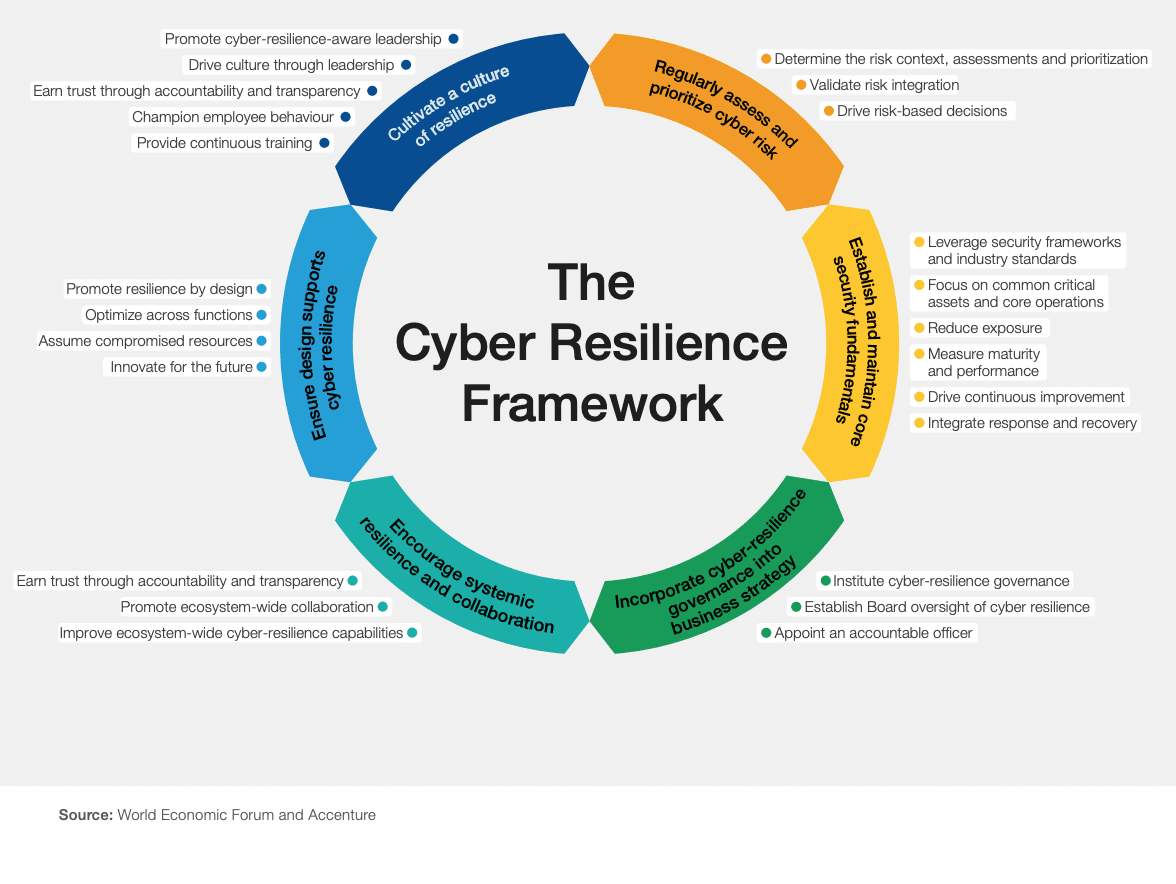
In today’s digital landscape, a robust cyber resilience strategy is essential for safeguarding organizational data against the increasing prevalence of cyber threats. With data protection becoming a top priority, organizations are investing in advanced technologies such as backup solutions and immutable backups to enhance their defenses. The rise of ransomware attacks demands not only preventative measures but also a focus on effective ransomware recovery plans that minimize potential disruptions. By integrating data encryption and other protective measures, businesses can ensure that their assets remain secure and recoverable, even in the face of adverse incidents. Developing a comprehensive approach ensures swift recovery, thereby reinforcing the organization’s ability to maintain continuity during and after any cyber event.
As businesses navigate the challenges posed by cybersecurity threats, establishing a resilient approach to information security is crucial. This involves a multifaceted focus on safeguarding against potential data breaches and ensuring rapid recovery options are readily available. Key components of this approach may include employing innovative backup technologies, utilizing data encryption methods, and adopting practices that reinforce data integrity and accessibility. As organizations increasingly prioritize their backup processes and their ability to recover from incidents, the concept of cyber fortification emerges as vital. By recognizing the need for solid defenses coupled with effective recovery strategies, companies can position themselves to successfully handle future cyber challenges.
Understanding the Importance of Cyber Resilience
In today’s digital landscape, cyber resilience has emerged as a critical focus for organizations striving to protect their most valuable asset—data. The increase in cyberattacks, particularly ransomware, has underscored the need for a robust strategy beyond mere prevention. Cyber resilience encompasses the ability not only to defend against attacks but also to effectively recover from them. This proactive approach ensures minimal disruption to business operations and promotes a faster return to normalcy after an incident. As organizations adopt a cyber resilience strategy, they begin to view their IT infrastructure as a dynamic entity that requires constant adaptation and improvement.
Building cyber resilience also involves a fundamental shift in mindset among IT leaders. Rather than simply strengthening perimeter defenses through firewalls and access controls, they must foster a culture of preparedness and recovery. This involves investing in modern backup technologies and ensuring that data protection measures are in place, including encryption and immutable backups. By prioritizing these elements within their cyber resilience framework, organizations can significantly enhance their ability to withstand cyber threats while safeguarding sensitive data and maintaining compliance with regulatory requirements.
Frequently Asked Questions
What is a cyber resilience strategy and why is it important for data protection?
A cyber resilience strategy is an approach that combines prevention, detection, and rapid recovery to ensure that organizations can withstand cyber attacks while minimizing disruption. In terms of data protection, this strategy emphasizes the need for robust backup technology, immutable backups, and data encryption, enabling vital information to remain secure and easily recoverable after an incident.
How do immutable backups enhance ransomware recovery as part of a cyber resilience strategy?
Immutable backups are essential in a cyber resilience strategy as they ensure that backup data cannot be altered or deleted by ransomware or other malicious actors. This read-only feature allows organizations to maintain a reliable version of their data that can be swiftly restored after an attack, significantly improving ransomware recovery times.
What role does data encryption play in a cyber resilience strategy?
Data encryption is a crucial element of a cyber resilience strategy as it protects sensitive information from unauthorized access. By encrypting backup data, organizations enhance their data protection efforts, ensuring that even if attackers breach their networks, accessing critical data remains extremely difficult and that recovery processes are compliant with industry regulations.
How can organizations optimize their backup technology for a cyber resilience strategy?
Organizations can optimize their backup technology by adopting all-flash backup solutions, which enable faster backups and recovery processes. Additionally, implementing deduplication techniques can reduce storage needs, while regular testing of backup integrity ensures that copies are reliable and recoverable as part of a comprehensive cyber resilience strategy.
What are offsite and offline backups, and how do they contribute to a cyber resilience strategy?
Offsite and offline backups are copies of data stored in different geographic locations or in disconnected systems. They are vital to a cyber resilience strategy as they protect against local system failures and attacks, ensuring a recoverable copy of data is always available. This redundancy is crucial for maintaining business continuity in the face of cyber threats.
Why is it necessary to focus on both prevention and recovery in a cyber resilience strategy?
Focusing solely on prevention is no longer sufficient due to the inevitability of cyber attacks. A robust cyber resilience strategy balances prevention with rapid recovery, preparing organizations not only to resist attacks but also to recover quickly and with minimal financial and operational impacts after an incident occurs.
What challenges do organizations face when implementing a cyber resilience strategy?
Organizations face several challenges in implementing a cyber resilience strategy, including outdated backup technologies, failed backups, and inadequate data encryption. These vulnerabilities can lead to significant data loss and extended downtime, making it essential to regularly assess and update resilience strategies to effectively counter threats.
How can a comprehensive cyber resilience strategy minimize downtime after a cyber attack?
A comprehensive cyber resilience strategy minimizes downtime by employing multiple layers of protection, such as immutable backups, encryption, and offsite storage. By ensuring backups are reliable and easily accessible, organizations can quickly restore operations, reducing the impact of an attack on overall business function.
What is the significance of testing backup integrity in a cyber resilience strategy?
Testing backup integrity is crucial in a cyber resilience strategy as it ensures that all backups are reliable and recoverable, regardless of their age. Regular validation helps identify issues before a cyber attack occurs, allowing organizations to maintain confidence that they can restore data smoothly when needed.
How does adopting a proactive approach to cyber resilience differ from a reactive stance?
Adopting a proactive approach to cyber resilience involves anticipating and preparing for potential cyber threats, including robust data protection measures like backup technology and encryption. In contrast, a reactive stance often focuses on responding to incidents after they occur, which can lead to extended downtime and greater overall impact on the organization.
| Key Point | Explanation |
|---|---|
| Value of Data | Data is now the most valuable asset for businesses, making it a primary target for cyber-attacks. |
| Cyber Attack Reality | Organizations must accept that cyber-attacks are inevitable and prepare for them accordingly. |
| Need for Cyber Resilience Strategy | A robust strategy must focus on prevention, rapid recovery, and resilience to maintain business continuity. |
| Vulnerabilities | Key challenges include outdated backup technologies and failures in data backups, which can lead to severe losses. |
| Importance of Backups | Effective cyber resilience relies heavily on data protection and backup technologies, ensuring compliance and operational uptime. |
| Technology Adoption | Organizations should utilize all-flash backups and immutable backups to enhance recovery capabilities. |
| Encryption and Deduplication | These practices protect backup data and enhance storage efficiency, allowing for more reliable data recovery. |
| Offsite Backup Strategy | Maintaining offsite backups ensures recovery even when local systems are compromised. |
| Future-proofing Resilience | A comprehensive approach involving technology and policies is crucial for building a resilient system. |
Summary
A cyber resilience strategy is essential in today’s digital landscape where organizations face increasing cyber threats. Emphasizing rapid recovery and robust data protection measures, such a strategy ensures that businesses can withstand attacks and recover quickly without incurring significant losses. By investing in modern technologies, such as all-flash backups and immutable storage solutions, and adopting practices like encryption and deduplication, companies can fortify their defenses. Furthermore, maintaining offsite backups enhances security and provides additional recovery options. Therefore, integrating a cyber resilience strategy is not just advisable; it is necessary for ensuring business continuity in the face of inevitable cyber adversities.