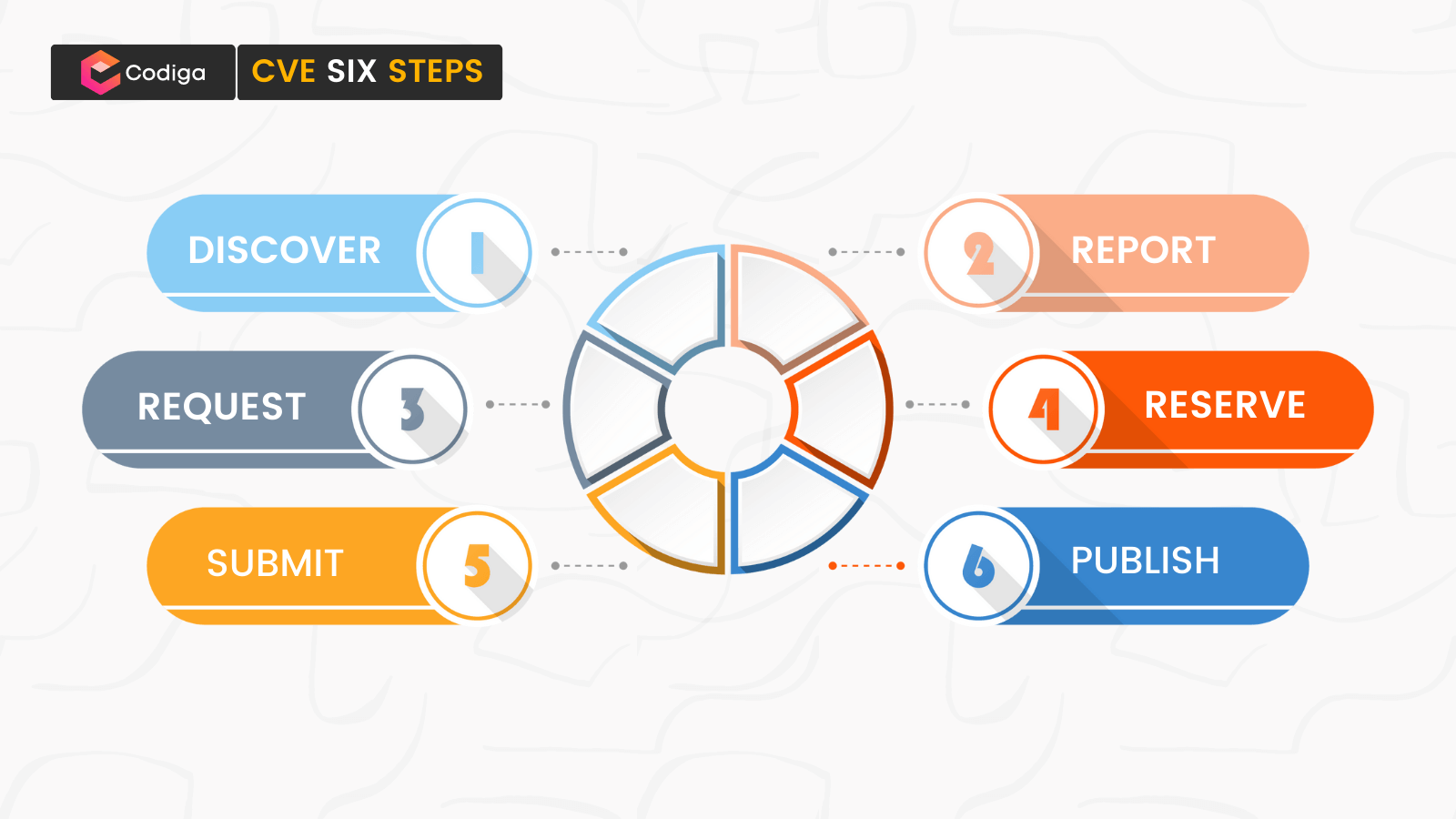
The CVE database, a cornerstone of cybersecurity vulnerabilities tracking, plays an integral role in safeguarding our digital world. For 25 years, the MITRE CVE program has provided a comprehensive resource that allows organizations to identify and address potential security threats effectively. However, recent developments regarding funding for the CVE database have raised concerns within the cybersecurity community. With MITRE’s contract with the US Department of Homeland Security not being renewed, the stability of this vital tool for open-source security hangs in the balance. As the landscape of cybersecurity funding evolves, the reliance on platforms like the CVE database becomes even more critical for DevSecOps tools aimed at enhancing software security and resilience.
Known as a vital repository of security vulnerabilities, the CVE database is essential for organizations striving to enhance their cybersecurity posture. This extensive collection of documented weaknesses aids teams in promptly identifying and mitigating risks, ensuring the integrity of their systems. The implications of changes in funding for such a critical resource could ripple across the industry, impacting everything from open-source security initiatives to the effectiveness of security measures in place. As the global cybersecurity framework shifts, the importance of comprehensive databases in managing threats remains paramount. Maintaining support for such initiatives is vital for fostering innovation in DevSecOps practices and securing funding sources that can ultimately safeguard our digital ecosystems.
The Importance of the CVE Database in Cybersecurity
The Common Vulnerabilities and Exposures (CVE) database plays a critical role in the landscape of cybersecurity by providing a standardized framework for identifying and addressing cybersecurity vulnerabilities. Maintaining an organized registry of vulnerabilities, the CVE database allows security professionals and developers to track known weaknesses and implement timely fixes. This is especially vital for organizations that rely on various software tools, as it helps them mitigate risks that could lead to exploitation by cybercriminals. The longevity and credibility of the CVE program underscore its importance as a foundational resource within the cybersecurity community.
With the integration of the CVE database into various security tools, organizations can benefit from a centralized source of information regarding vulnerabilities. This has allowed for the faster deployment of patches within development pipelines, particularly benefiting DevSecOps teams. However, reliance on a single source of vulnerability data also poses risks, as any disruptions to this resource could significantly hamper the security efforts of organizations that depend on it for daily operations.
Frequently Asked Questions
What is the CVE database and why is it important in cybersecurity?
The CVE (Common Vulnerabilities and Exposures) database is a crucial resource in the cybersecurity landscape, providing a unified means to identify and track cybersecurity vulnerabilities. Managed by the MITRE organization, the CVE database is integral for DevSecOps tools and open-source security practices, helping secure various software applications. Its comprehensive listings enable organizations to respond effectively to vulnerabilities, making it vital for protecting information systems against cyber threats.
How does the CVE database support DevSecOps practices?
The CVE database supports DevSecOps practices by providing a centralized repository of known vulnerabilities that teams can use to secure their software development processes. This resource allows DevSecOps teams to quickly identify, assess, and deploy fixes for vulnerabilities within their applications, improving the overall security posture. The integration of CVE data into development pipelines enhances the efficiency of vulnerability management, which is indispensable in today’s fast-paced software delivery environment.
What are the implications of government funding withdrawal for the CVE database?
The withdrawal of government funding for the CVE database raises concerns about its future sustainability and operational integrity. Experts fear that without adequate support, the quality and reliability of this critical resource could decline, making it more challenging for organizations to stay ahead of cyber threats. Potential funding shifts to private sector organizations may also lead to worries about monopolization and control over essential cybersecurity information, which typically benefits the broader community.
What alternatives exist if the CVE database becomes unavailable?
If the CVE database becomes unavailable, organizations can resort to alternatives such as vendor-specific vulnerability databases or the National Vulnerability Database (NVD). However, these options may lack the comprehensiveness and centralized structure that MITRE’s CVE program provides. Therefore, while viable, they may require organizations to adapt their vulnerability management processes to accommodate the differences in database characteristics.
What should the cybersecurity community do about the future of the CVE database?
The cybersecurity community should advocate for continued funding and support for the CVE database while exploring alternative solutions, such as crowdfunding initiatives or the formation of a community-driven advisory board. Engaging stakeholders from both public and private sectors to ensure the longevity and reliability of the CVE program is crucial. Monitoring developments closely and participating in discussions around its future can help protect this invaluable resource.
Why is the CVE database considered the most widely used resource for identifying vulnerabilities?
The CVE database is regarded as the most widely used resource for identifying vulnerabilities due to its long-standing reputation for reliability, centralized organization, and comprehensive coverage of known security issues. This status, managed by MITRE, ensures that users receive consistent and up-to-date information essential for addressing cybersecurity vulnerabilities. Its role in supporting open-source security and resource allocation for awareness campaigns further underlines its importance in the cybersecurity landscape.
| Key Points | Details |
|---|---|
| CVE Database Overview | The CVE database tracks vulnerabilities and has been essential for cybersecurity for 25 years. |
| MITRE’s Role | MITRE has been responsible for maintaining the CVE database, with funding from the US government. |
| Funding Concerns | The contract for funding with the US Department of Homeland Security has not been renewed, leading to concerns in the cybersecurity community. |
| Community Reaction | Experts express that losing the CVE resource could benefit cybercriminals and complicate software security efforts. |
| Potential Solutions | There are suggestions for crowdfunding or creating a community board to sustain the CVE database and adapt its management. |
| Current Status | As of now, the contract has reportedly been extended, assuring the CVE database’s continued operation in the short term. |
| Future Considerations | The situation highlights the necessity for a diversified information network in cybersecurity, rather than relying solely on MITRE’s CVE database. |
Summary
The CVE database serves as a critical framework for identifying and managing cybersecurity vulnerabilities. It is imperative for organizations, as it assists them in mitigating risks and reinforcing security protocols. The current funding uncertainties surrounding the CVE database under MITRE should prompt the industry to consider alternative solutions and funding models to safeguard this vital resource. Activating community support and encouraging a multi-source approach will be essential to fortifying the future of vulnerability management in cybersecurity.